Defend
Internet Exposure Monitoring
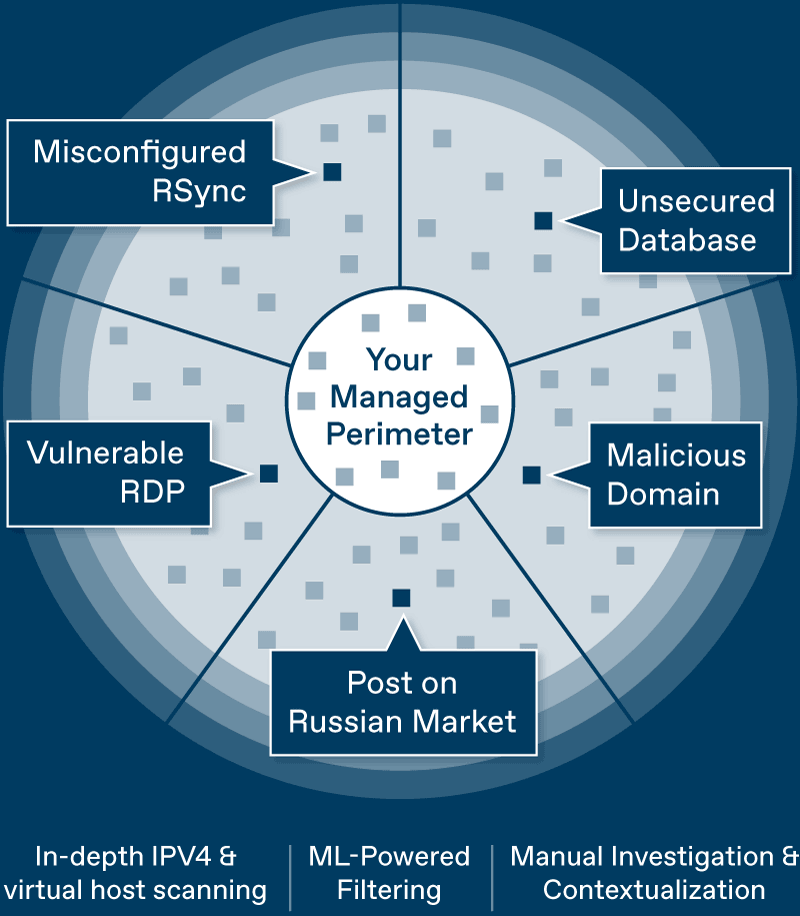
Advancing digitalization is increasing outsourcing, cloud usage, and connected devices—and with it, digital footprints and risks. DCSO proactively identifies and monitors external attack surfaces, protects brands and reputations, and prioritizes high-risk areas. Our Internet Exposure Monitoring (IEM) modules detect, analyze, and report external risks early on— for a strong sense of security.
24/7/365 Visibility
We continuously monitor countless sources in the digital environment around the clock, 365 days a year, to provide you with a complete picture of potential external risks and threats at all times. This ensures that you won't miss any threats, no matter when or where they arise.
Prioritization
No information overload—just the essentials. Our algorithms detect and filter out suspicious signals. Our experienced analysts review each alert, assess its relevance, and prepare it so that you only receive clear, understandable, and actionable information that is truly important.
Capacity to Act and Defense
From warning to solution: Each notification contains the necessary context, specific details, and clear recommendations for action. This enables you to identify and address risks in a targeted and efficient manner before they cause real damage.
Holistic Approach
Our Internet Exposure Monitoring (IEM) modules detect, analyze, and report on external risks early on, providing you with a strong sense of security. Additionally, based on their knowledge and experience, our (human) analysts reduce any unnecessary noise, separating the important from the unimportant.
Simply select the modules you want for monitoring according to your needs. We will be happy to advise you on your selection!
Information Leakage Monitoring (ILM)
Our Information Leakage Monitoring module detects sensitive information that has been published online, either accidentally or intentionally.
We perform regular checks:
-
All publicly accessible IPv4 addresses for unsecured storage or databases containing sensitive data.
-
It also checks publicly accessible content on web links from sharing platforms, cloud storage, code sharing, file sharing tools, and SaaS project management solutions.
-
We also take into account content that third parties (customers, partners, suppliers, subcontractors, etc.) with access to sensitive data could store.
Your security comes first:
-
We provide proactive protection against the use of compromised data by criminals.
-
We ensure the confidentiality of sensitive information.
-
Defense against digital risks posed by third parties, protection of intellectual property, legal compliance, and brand reputation.
-
Information leakage monitoring safeguards companies against digital risks posed by third parties, including the loss of intellectual property and other confidential information due to insecure internal or external infrastructures, legal liability under data protection laws, and reputational damage.
Identity Leakage Monitoring (IDLM)
The Identity Leakage Monitoring module detects when company data or identities are compromised, such as through data leaks, breaches, theft, or publication on the dark web. Detection is based on a list of email domains provided by the customer.
How it works:
-
First, automated preprocessing of scan results occurs (data cleansing, duplicate checking, and sorting out irrelevant data). Then, a clear, actionable evaluation is provided.
-
The timeliness and relevance of the data are assessed for efficient remediation.
Additional functions include:
-
Detecting company access data exfiltrated by malware in the info-stealer category.
-
If available, we provide the following compromised data: email addresses, plaintext passwords, target URLs, IP addresses of infected devices, and the date of infection.
Threats covered:
-
Phishing, hostile account takeovers, and ransomware attacks.
Dark Web Monitoring incl. Ransomwatch
Stay one step ahead of the threat. Our Dark Web module scans hundreds of sources continuously, including Tor forums, illegal darknet marketplaces, and instant messaging platforms such as Telegram, IRC, and Discord. This allows you to detect the following at an early stage:
-
Fraudulent schemes and attacks affecting your business
-
Exploitation of vulnerabilities and data leaks
-
The dissemination of confidential information or personal data
RansomWatch Extension:
-
Proactive risk management in the supply chain. Receive relevant alerts when suppliers or partners are affected by ransomware.
-
Providing a list of keywords (ideally domain names) from your supply chain can help improve your resilience to ransomware and supply chain risks.
Asset Discovery & Monitoring (ADM)
Detect Shadow IT Early: DM’s Asset Discovery & Monitoring regularly analyzes the entire IPv4 address space for publicly accessible assets, including devices, domains, FQDNs, and web services. This analysis includes IT, IoT, and OT infrastructures that are outside the view of your central IT team.
What you get:
-
Shadow IT identification: An assessment of which assets operate outside direct IT control or pose a cyber hygiene risk.
-
Vulnerability scan: Passive testing of identified assets for serious security vulnerabilities.
-
Threats: Protection against footprinting, infrastructure intrusion, data theft, and ransomware.
Domain Protection
Domain Protection safeguards your brand against identity theft by identifying and eliminating fraudulent domains and typosquatting domains, also known as typo domains.
Real-time DNS monitoring worldwide:
-
It analyzes which domain names are being queried.
-
It detects latent threats and domain and mail server setups through continuous DNS monitoring.
Abuse detection:
-
Identifies alternative versions of legitimate domains (e.g., inversions, split twists, and subdomains) to uncover phishing, counterfeiting, and parking.
ContaCt